CLOUD SECURITY ALLIANCE
Introduction
 The introduction of Connected Vehicles (CVs) has been discussed for many years. Pilot implementations currently underway are evaluating CV operations in realistic municipal environments. CVs are beginning to operate in complex environments composed of both legacy and modernized traffic infrastructure. Security systems, tools and guidance are needed to aid in protecting CVs and the supporting infrastructure. Recent headlines, such as the infamous Jeep hack and Tesla hack, demonstrate just how critical it is to ensure the security of CVs. Hackers’ ability to hijack control of CVs is now proven very real.
The introduction of Connected Vehicles (CVs) has been discussed for many years. Pilot implementations currently underway are evaluating CV operations in realistic municipal environments. CVs are beginning to operate in complex environments composed of both legacy and modernized traffic infrastructure. Security systems, tools and guidance are needed to aid in protecting CVs and the supporting infrastructure. Recent headlines, such as the infamous Jeep hack and Tesla hack, demonstrate just how critical it is to ensure the security of CVs. Hackers’ ability to hijack control of CVs is now proven very real.
The authorities have taken notice of the risk. On March 17, 2016, a joint public service announcement by the FBI, Department of Transportation (DoT) and the National Highway Traffic and Safety Administration (NHTSA), warned of the threat of Internet-based attacks on cars and trucks. While the FBI noted that the vulnerabilities identified so far have been addressed, it is important that CV consumers and manufacturers be continually aware of the inevitability of future vulnerabilities. Going forward, we can probably expect to see the same level of regulation as for critical infrastructures. Some lawmakers, such as the state of Michigan, are already considering laying out the foundations of legislation and sentencing guidelines for the crime of car hacking.
The Department of Transportation Federal Highway Administration (FHWA) has developed a Connected Vehicle Reference Implementation Architecture (CVRIA). CVRIA defines four architectural views — Enterprise, Functional, Physical, and Communications — with security integrated throughout each view. Review of the CVRIA provides a solid understanding of the applications, connectivity and components associated with the overarching CV ecosystem.
One of the primary capabilities enabled by the CV architecture is the ability of vehicles to communicate with proximal vehicles (“V2V”), with infrastructure (“V2I”), and with applications (“V2X”). Communication is accomplished through a wireless messaging protocol known as Dedicated Short Range Communication (DSRC). DSRC messages are digitally signed to guard against tampering and spoofing.
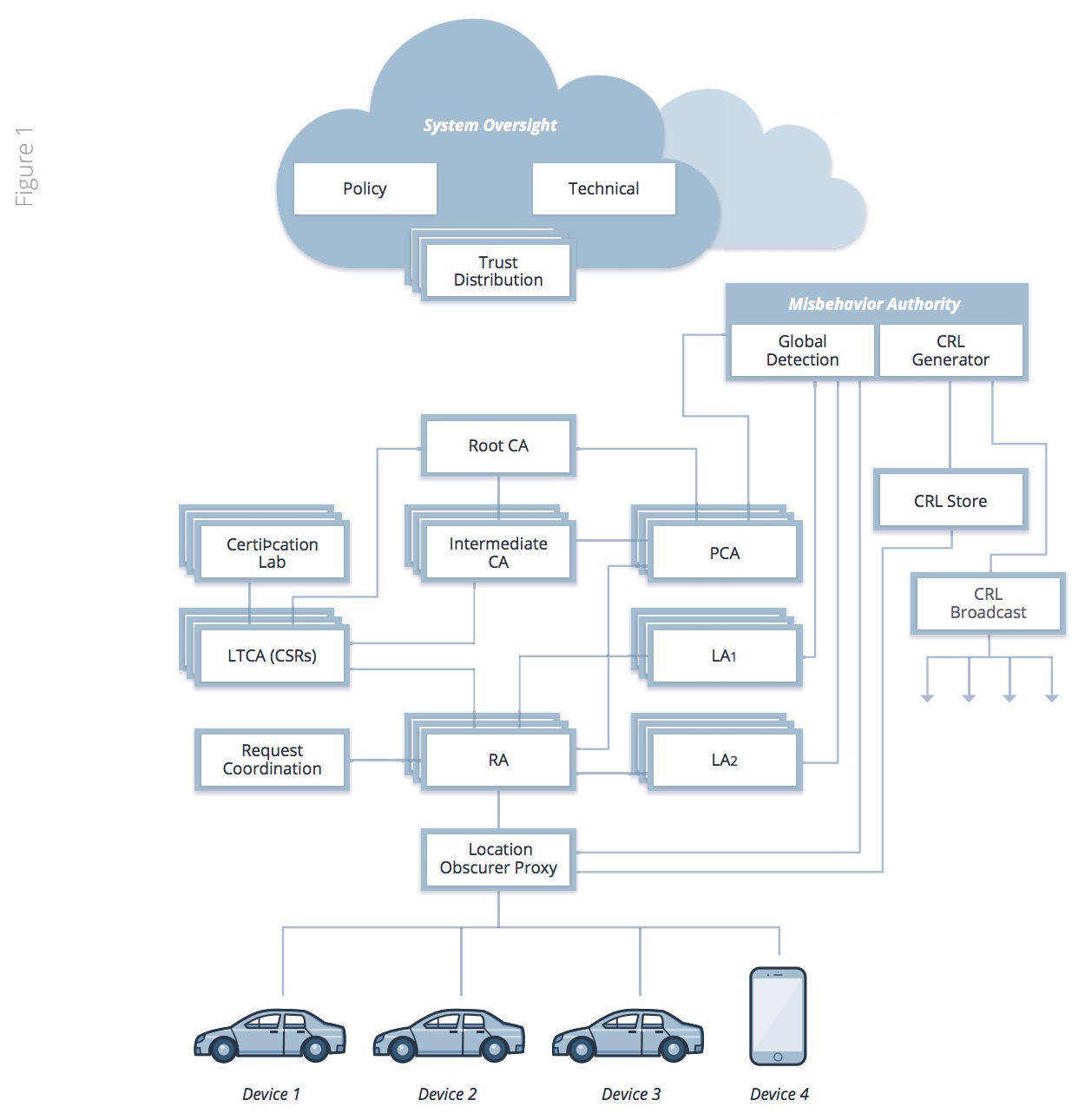
The digital signatures are enabled by certificates provisioned to each component from an infrastructure known as the Security Credential Management System (SCMS). The SCMS is a proof-of-concept Public Key Infrastructure (PKI) tailored to provision certificates to vehicles and infrastructure. SCMS implements robust privacy controls that guard against both message manipulation and casual tracking of vehicles (and by extension, their owners) by unauthorized parties (the “outsider threat”). It also protects against rogue parties that operate components of the SCMS itself (the “insider threat”). The SCMS employs components such as Location Obscurer Proxies (LOPs) that shield vehicle identities from PKI components and vehicle operators. Vehicles employ rotating certificates taken from a pool, and then use them to digitally sign messages. The SCMS design is depicted in Figure 1 (reference)
Work is also being done to support secure vehicle operations. In July 2016, the Auto Information Sharing and Analysis Center (ISAC) published a report titled “Automobile Security Best Practices.” The report provides a well-thought-out set of recommendations for securing vehicle operation platforms.
Other industry work focuses on helping Original Equipment Manufacturers (OEMs) and suppliers understand the threats associated with vehicles. Industry groups such as I AM The Cavalry have released guidance to this effect, for example, the Five Star Automotive Cyber Safety Program.
Looking at the Bigger Picture
When we consider the future of automobile technology, it is important to take a “big picture” view of the various aspects of vehicles and infrastructure components to better understand their interrelationships, dependencies and threats to the traffic ecosystem. In the future:
- CVs will operate while communicating with both legacy and modernized traffic infrastructures and their sensors.
- Traffic Management applications and vehicles will interact with cloud services using a mixed set of transport protocols (RF/ WiFi, etc).
- OEM and 3rd party applications will be installed on vehicle platforms and traffic infrastructure components to provide enhanced capabilities.
- CVs will integrate with the IoT ecosystem to support vehicle integration with smart homes and smart businesses.
As in other industries, innovation will abound as methods and capacities for connectivity rise. We anticipate full integration of CVs with the IoT, which presents all new security challenges.
Next we analyze the evolution of vehicle connectivity towards fully connected and autonomous systems. We then provide recommendations for enterprise-wide security controls to safeguard the driving public. Finally, we evaluate the security gaps that need attention. Our intent is to provide a comprehensive perspective on vehicle security design, which must be flexible enough to adapt to future challenges, and be cognizant of unanticipated threats that future disruptive technologies may bring.
Download full version (PDF): Observations and Recommendations on Connected Vehicle Security
About the Cloud Security Alliance
cloudsecurityalliance.org
The Cloud Security Alliance (CSA) is the world’s leading organization dedicated to defining and raising awareness of best practices to help ensure a secure cloud computing environment. CSA harnesses the subject matter expertise of industry practitioners, associations, governments, and its corporate and individual members to offer cloud security-specific research, education, certification, events and products.
Tags: Connected Vehicles, CVs, Hacking, safety, Security, Tesla Hack






 RSS Feed
RSS Feed